Key Industry Statistics:
- 60% of healthcare data breaches in 2023 involved communication systems
- Healthcare organizations face average HIPAA violation fines of $50,000 per incident
- 89% of healthcare providers report improved response times with secure VoIP systems
- $2.3M: Average cost of a healthcare data breach in 2023
Healthcare communication failures contribute to 70% of medical errors, according to a recent Joint Commission report. When patient lives and privacy are on the line, secure, efficient communication isn’t just a requirement—it’s a critical lifeline. Modern HIPAA-compliant VoIP solutions offer healthcare providers the perfect balance of security and speed, while potentially reducing communication costs by up to 50%.
Mastor Telecom’s Healthcare VoIP Solutions
As St. Louis’s leading provider of HIPAA-compliant communication systems, Mastor Telecom delivers:
Security Features
- 256-bit AES encryption for all voice and data transmissions
- Two-factor authentication for all system access
- Regular security audits and penetration testing
- Automated security patch management
- 24/7 network monitoring
Healthcare-Specific Capabilities
- Integration with major EMR systems including Epic, Cerner, and Allscripts
- Mobile health app compatibility
- Telemedicine platform integration
- Emergency department priority routing
- Nurse call system integration
HIPAA Requirements and Compliance
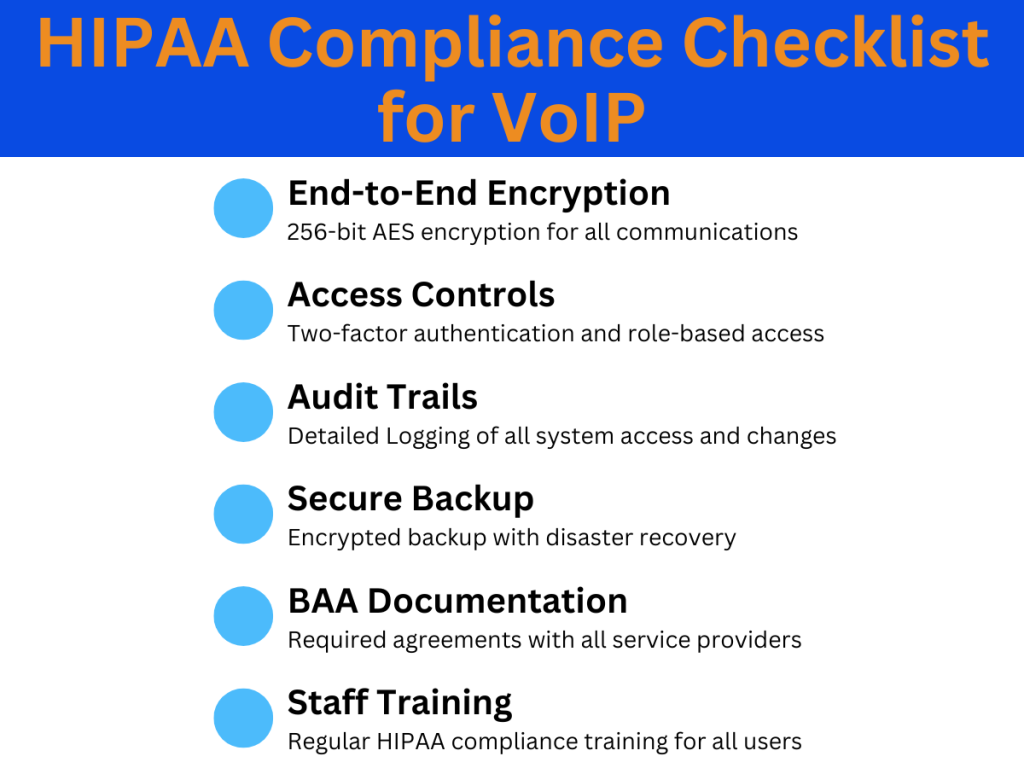
Critical Requirements
- Encryption requirements for PHI
- Access control protocols
- Activity logging and monitoring
- Device security policies
- Emergency access procedures
Violation Consequences
- Tier 1: $100-$50,000 per violation (unknown/reasonable cause)
- Tier 2: $1,000-$50,000 per violation (willful neglect)
- Tier 3: $10,000-$50,000 per violation (willful neglect, uncorrected)
- Criminal charges possible for serious breaches
Solutions for Different Healthcare Settings
Hospital Systems
- Multi-department routing
- Code system integration
- Specialist on-call management
- OR/ER priority communications
- Mass notification capabilities
Medical Practices
- Patient appointment reminders
- Secure messaging between providers
- Electronic faxing integration
- Mobile device management
- BYOD security protocols
Specialty Clinics
- Custom workflow automation
- Specialized department routing
- Remote consultation tools
- Patient portal integration
- Secure file sharing
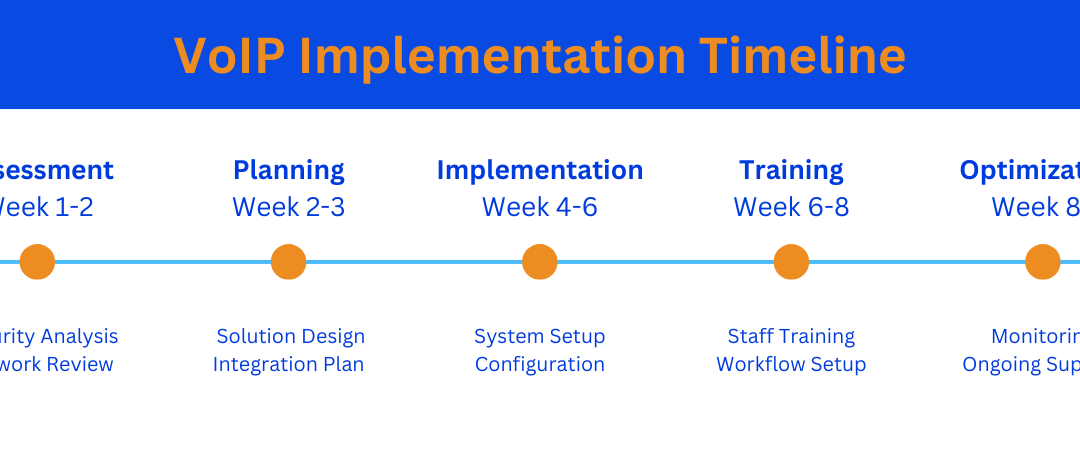
Implementation Process and Timeline
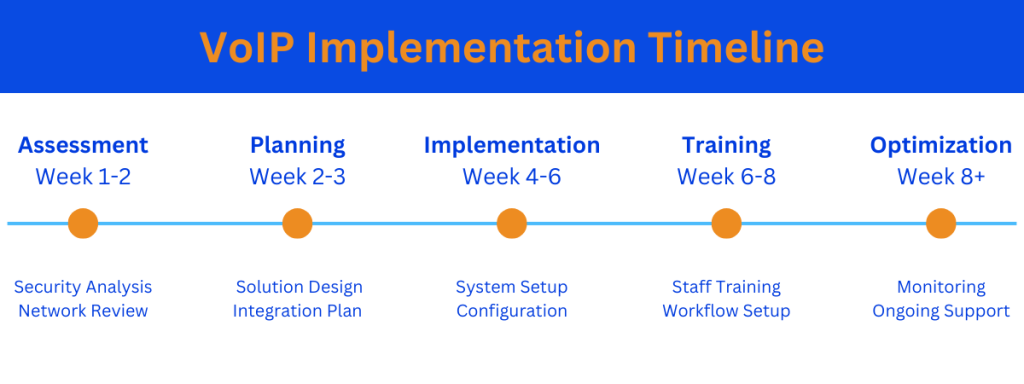
- Assessment Phase (Week 1-2)
- Security risk evaluation
- Network infrastructure analysis
- Workflow documentation
- Compliance gap identification
- Planning Phase (Week 2-3)
- Custom solution design
- Integration planning
- Training schedule development
- Compliance documentation preparation
- Implementation Phase (Week 4-6)
- Network security setup
- System installation
- Integration configuration
- Initial testing
- Training Phase (Week 6-8)
- Staff security training
- Workflow education
- Compliance protocol review
- Emergency procedure training
- Optimization Phase (Week 8+)
- Performance monitoring
- System fine-tuning
- Ongoing support
- Regular compliance audits
Technical Specifications and Security Infrastructure
Network Security Layer
- Enterprise-grade firewalls with IDS/IPS
- VLAN segregation for voice traffic
- Real-time threat monitoring
- Automated backup systems with 99.999% uptime
- Geo-redundant data centers
Encryption and Authentication Primary Security Protocols:
- TLS 1.3 for signaling
- SRTP for media encryption
- OAuth 2.0 for authentication
- Zero-trust architecture
- Regular penetration testing
Disaster Recovery
- Automatic failover systems
- 4-hour maximum recovery time objective (RTO)
- 15-minute recovery point objective (RPO)
- Daily encrypted backups
- Annual DR testing and validation
Choosing the Right Healthcare VoIP Provider
When selecting a VoIP provider for your healthcare facility, consider:
- HIPAA compliance expertise
- Security feature set
- Integration capabilities
- Support availability
- Scalability options
- Cost structure
Ready to Secure Your Healthcare Communications?
Contact Mastor Telecom today to learn how our HIPAA-compliant VoIP solutions can enhance your healthcare facility’s communication while maintaining strict security standards. Our team of experts will work with you to design a system that meets your specific needs and compliance requirements.
Schedule a consultation to:
- Assess your current communication system
- Identify potential security risks
- Develop a custom implementation plan
- Review pricing options
- Discuss compliance requirements
Frequently Asked Questions
Q: How does VoIP ensure HIPAA compliance? A: Our VoIP system ensures HIPAA compliance through end-to-end encryption, secure access controls, comprehensive audit trails, and regular security updates. We provide BAA agreements and maintain strict security protocols exceeding HIPAA requirements.
Q: Can we keep our existing phone numbers? A: Yes, Mastor Telecom provides seamless number porting for all existing phone lines while maintaining continuous service during transition.
Q: What happens during power outages? A: Our systems include battery backup and automatic failover to mobile devices, ensuring continuous communication even during power disruptions.
Q: How long does implementation take? A: Typical implementation takes 6-8 weeks from initial assessment to full deployment, with zero downtime during transition.